Honeywell – Honeywell Transforms Building Management with First-of-its-Kind Technology
New platform features built-in cybersecurity, faster network speeds and innovative technology to address building managers’ concerns and strategies
ATLANTA, Jan. 23, 2024 /PRNewswire/ — Honeywell (NASDAQ: HON) today launched Advance Control for Buildings, a groundbreaking platform marking one of the company’s most substantial leaps in building controls innovation to date.
Designed to automate building management and provide the foundation for a building’s energy efficiency strategy, Advance Control combines the latest technologies with decades of innovation and domain expertise. Automation and machine learning fuel a streamlined operation system featuring built-in cybersecurity and technology to deliver faster network speeds that, in an industry first, uses existing wiring. This announcement further supports Honeywell’s recently announced plans to realign its business with three compelling megatrends, including automation and energy transition.
“Today, buildings are facing mounting pressures around safety, operational efficiency and energy efficiency. By pushing the boundaries of technological advancement, Advance Control not only helps building managers optimize their building operations to meet these pressures, but also champions innovation,” said Steve Kenny, vice president and general manager, Honeywell Building Management Systems. “Automation breaks down operational barriers to give building managers more control over the efficiency of their buildings, ultimately helping improve the occupant experience while advancing energy management goals.”
As part of this rollout, Honeywell recently announced strategic alliances with two semiconductor leaders, NXP® Semiconductors N.V. (NASDAQ: NXPI) and Analog Devices, Inc.(NASDAQ: ADI) to streamline the transition to intelligent edge processing. With NXP, Honeywell seeks to elevate machine learning and autonomous decision-making for enhanced energy management and convenience, as well as enhanced security within and beyond the building. The joint efforts with ADI aim to deliver more efficiency and increased intelligence through digital connectivity and advanced signal conversion across many industrial applications.
“As the building automation market demands greater digital connectivity and security enabling data driven efficiencies, ADI has invested in new technologies meeting these needs while also offering flexibility for future upgrades. Our single-pair Ethernet (T1L) enables the possibility of reusing a building’s existing wiring, helping to reduce installation time, cost, and waste. ADI is pleased to work with Honeywell to bring this new technology to building management systems for the first time in Advance Control for Buildings,” said Diarmuid McSwiney, Managing Director, Industrial Connectivity and Control at ADI.
“Security resilience is increasingly required for networked control systems,” said Rafael Sotomayor, Executive Vice President and General Manager, Secure Connected Edge, NXP Semiconductors. “Honeywell’s Advance Control for Buildings platform leverages NXP processors that efficiently combine machine learning with advanced security technologies to protect sensitive building automation infrastructure.”
According to the UN Environment Programme, buildings account for 37% of global CO2 emissions[i], resulting in increasing pressure to identify and reduce energy use. At the same time, the lack of skilled labor makes it difficult for building owners to find technicians to upkeep and modernize spaces.
“Real estate and facilities leaders are placing top priority on optimizing building operations,” said Sandy Rogers, a principal analyst with Verdantix, a research and advisory firm. “Organizations require greater visibility and automated control across their building portfolios, and they will increasingly look to digital innovations such as AI and machine learning for added intelligence.”
SourceHoneywell
EMR Analysis
More information on Honeywell: See the full profile on EMR Executive Services
More information on Vimal Kapur (Chief Executive Officer, Honeywell): See the full profile on EMR Executive Services
More information on Advance Control for Buildings by Honeywell: https://buildings.honeywell.com/us/en/solutions/advance-control + Building owners face new challenges, from cyber threats via their OT systems, to scarcity of skilled technicians, to new sustainability targets. So we’ve set out to reimagine building controller design. Automation and machine learning fuel a streamlined operation system featuring built-in cybersecurity and technology to deliver faster network speeds that, in an industry first, uses existing wiring.
More information on Honeywell Building Automation Segment (BA): Through hardware, software, sensors, and analytics, Honeywell helps customers convert buildings into integrated, safe, and more sustainable assets. With solutions and services used in more than 10 million buildings worldwide, Building Automation will continue to strengthen Honeywell’s position in attractive end markets like hospitals, airports, education, and data centers.
More information on Billal Hammoud (President and Chief Executive Officer, Building Automation Segment (BA), Honeywell): See the full profile on EMR Executive Services
More information on Honeywell Building Management Systems (BMS): See the full profile on EMR Executive Services + The next level of HVAC efficiency.
Optimize building operations affordably by customizing control processes, sharing information across departments and improving response time. Using our comprehensive range of controllers, field devices and software, we’ll help you customize a system to fit your building and your future.
We Aim To Exceed Your Expectations Of What A Building Management System Can Do
More information on Steve Kenny (Vice President & General Manager, Building Management Systems, Honeywell Building Systems, Honeywell Building Automation Segment, Honeywell): See the full profile on EMR Executive Services
More information on NXP: http://www.nxp.com/ + NXP Semiconductors N.V. (NASDAQ: NXPI) enables a smarter, safer and more sustainable world through innovation. As a world leader in secure connectivity solutions for embedded applications, NXP is pushing boundaries in the automotive, industrial & IoT, mobile, and communication infrastructure markets. Built on more than 60 years of combined experience and expertise, the company has approximately 34,500 employees in more than 30 countries and posted revenue of $13.21 billion in 2022.
More information on Kurt Sievers (President & Chief Executive Officer, NXP): https://www.nxp.com/company/about-nxp/leadership-team:NXP-LEADERSHIP + https://www.linkedin.com/in/kurt-sievers/
More information on Rafael Sotomayor (Executive Vice President and General Manager, Secure Connected Edge, NXP): https://www.nxp.com/company/about-nxp/leadership-team:NXP-LEADERSHIP + https://www.linkedin.com/in/rafael-sotomayor-09bb9/
More information on Analog Devices (ADI): https://www.analog.com/en/index.html + Analog Devices, Inc. (NASDAQ: ADI) is a global semiconductor leader that bridges the physical and digital worlds to enable breakthroughs at the Intelligent Edge. ADI combines analog, digital, and software technologies into solutions that help drive advancements in digitized factories, mobility, and digital healthcare, combat climate change, and reliably connect humans and the world. With revenue of more than $12 billion in FY22 and approximately 25,000 people globally working alongside 125,000 global customers, ADI ensures today’s innovators stay Ahead of What’s Possible.
More information on Vincent Roche (Chair of the Board of Directors & Chief Executive Officer, Analog Devices (ADI)): https://www.analog.com/en/about-adi/corporate-information/executive-team/vincent-roche.html
More information on Diarmuid McSwiney (Managing Director, Industrial Connectivity and Control, Analog Devices (ADI)): https://www.linkedin.com/in/diarmuidmcswiney/
More information on the UN Environment Programme (UNEP): https://www.unep.org/ + Since its inception in 1972, the United Nations Environment Programme (UNEP) has been the global authority that sets the environmental agenda, promotes the coherent implementation of the environmental dimension of sustainable development within the United Nations system and serves as an authoritative advocate for the global environment.
UNEP’s mission is to provide leadership and encourage partnership in caring for the environment by inspiring, informing, and enabling nations and peoples to improve their quality of life without compromising that of future generations.
More information on Verdantix: https://www.verdantix.com/ + Verdantix is a research and advisory firm that acts as an essential thought-leader for world-enhancing innovation. Together with our clients, we shape markets, define the technologies of tomorrow and futureproof businesses.
More information on David Metcalfe (Chief Executive Officer, Verdantix): https://www.verdantix.com/analyst/david-metcalfe + https://www.linkedin.com/in/david-metcalfe-08352b1/
More information on Sandy Rogers (Principal Analyst, Verdantix): https://www.verdantix.com/analyst/sandy-rogers + https://www.linkedin.com/in/sandyrogers/
EMR Additional Notes:
- Cybersecurity:
- Computer security, cybersecurity, or information technology security is the protection of computer systems and networks from information disclosure, theft of or damage to their hardware, software, or electronic data, as well as from the disruption or misdirection of the services they provide.
- Ransomware strike: Ransomware attacks work by gaining access to your computer or device, and then locking and encrypting the data stored on it. How does this happen? It often happens when victims mistakenly download malware through email attachments or links from unknown sources, which happen to be hackers.
- Data breach:
- A data breach is a security violation, in which sensitive, protected or confidential data is copied, transmitted, viewed, stolen or used by an individual unauthorized to do so. Other terms are unintentional information disclosure, data leak, information leakage, and data spill.
- Cyber Attack:
- Targeting an enterprise’s use of cyberspace for the purpose of disrupting, disabling, destroying, or maliciously controlling a computing environment/infrastructure; or destroying the integrity of the data or stealing controlled information.
- Malware:
- Malware, or malicious software, is any program or file that is intentionally harmful to a computer, network or server. Types of malware include computer viruses, worms, Trojan horses, ransomware and spyware.
- Penetration Testing:
- Penetration testing (or pen testing) is a security exercise where a cyber-security expert attempts to find and exploit vulnerabilities in a computer system. The purpose of this simulated attack is to identify any weak spots in a system’s defenses which attackers could take advantage of.
- Phishing:
- Phishing attacks are fraudulent emails, text messages, phone calls or web sites designed to trick users into downloading malware, sharing sensitive information or personal data (e.g., Social Security and credit card numbers, bank account numbers, login credentials), or taking other actions that expose themselves or their organizations to cybercrime. Successful phishing attacks often lead to identity theft, credit card fraud, ransomware attacks, data breaches, and huge financial losses for individuals and corporations.
- Air Gapping:
- An air gap is a security measure that involves isolating a computer or network and preventing it from establishing an external connection. An air-gapped computer is physically segregated and incapable of connecting wirelessly or physically with other computers or network devices.
- Cloud Computing:
- Cloud computing is a general term for anything that involves delivering hosted services over the internet. … Cloud computing is a technology that uses the internet for storing and managing data on remote servers and then access data via the internet.
- Cloud computing is the on-demand availability of computer system resources, especially data storage and computing power, without direct active management by the user. Large clouds often have functions distributed over multiple locations, each location being a data center.
- Edge Computing:
- Edge computing is a form of computing that is done on site or near a particular data source, minimizing the need for data to be processed in a remote data center.
- Edge computing can enable more effective city traffic management. Examples of this include optimising bus frequency given fluctuations in demand, managing the opening and closing of extra lanes, and, in future, managing autonomous car flows.
- An edge device is any piece of hardware that controls data flow at the boundary between two networks. Edge devices fulfill a variety of roles, depending on what type of device they are, but they essentially serve as network entry — or exit — points.
- There are five main types of edge computing devices: IoT sensors, smart cameras, uCPE equipment, servers and processors. IoT sensors, smart cameras and uCPE equipment will reside on the customer premises, whereas servers and processors will reside in an edge computing data centre.
- In service-based industries such as the finance and e-commerce sector, edge computing devices also have roles to play. In this case, a smart phone, laptop, or tablet becomes the edge computing device.
- Data Centers:
- A data center is a facility that centralizes an organization’s shared IT operations and equipment for the purposes of storing, processing, and disseminating data and applications. Because they house an organization’s most critical and proprietary assets, data centers are vital to the continuity of daily operations.
- Hyperscale Data Centers:
- The clue is in the name: hyperscale data centers are massive facilities built by companies with vast data processing and storage needs. These firms may derive their income directly from the applications or websites the equipment supports, or sell technology management services to third parties.
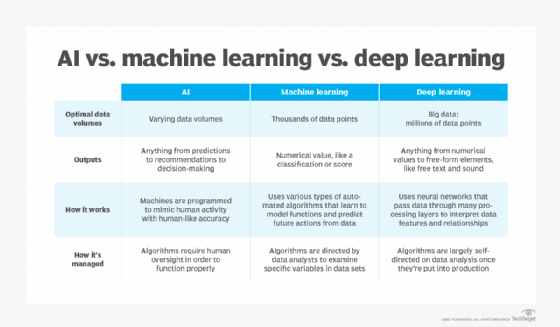
- AI – Artificial Intelligence:
- https://searchenterpriseai.techtarget.com/definition/AI-Artificial-Intelligence +
- Artificial intelligence is the simulation of human intelligence processes by machines, especially computer systems. Specific applications of AI include expert systems, natural language processing, speech recognition and machine vision.
- As the hype around AI has accelerated, vendors have been scrambling to promote how their products and services use AI. Often what they refer to as AI is simply one component of AI, such as machine learning. AI requires a foundation of specialized hardware and software for writing and training machine learning algorithms. No one programming language is synonymous with AI, but a few, including Python, R and Java, are popular.
- In general, AI systems work by ingesting large amounts of labeled training data, analyzing the data for correlations and patterns, and using these patterns to make predictions about future states. In this way, a chatbot that is fed examples of text chats can learn to produce lifelike exchanges with people, or an image recognition tool can learn to identify and describe objects in images by reviewing millions of examples.
- AI programming focuses on three cognitive skills: learning, reasoning and self-correction.
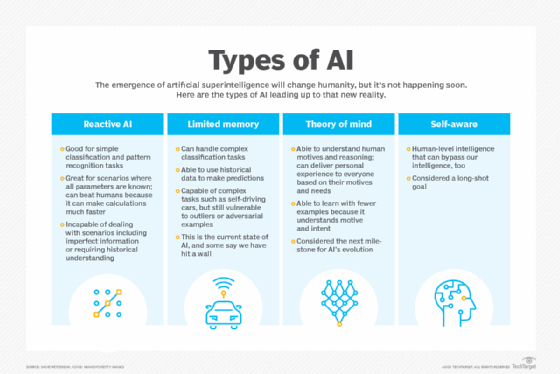
- What are the 4 types of artificial intelligence?
- Type 1: Reactive machines. These AI systems have no memory and are task specific. An example is Deep Blue, the IBM chess program that beat Garry Kasparov in the 1990s. Deep Blue can identify pieces on the chessboard and make predictions, but because it has no memory, it cannot use past experiences to inform future ones.
- Type 2: Limited memory. These AI systems have memory, so they can use past experiences to inform future decisions. Some of the decision-making functions in self-driving cars are designed this way.
- Type 3: Theory of mind. Theory of mind is a psychology term. When applied to AI, it means that the system would have the social intelligence to understand emotions. This type of AI will be able to infer human intentions and predict behavior, a necessary skill for AI systems to become integral members of human teams.
- Type 4: Self-awareness. In this category, AI systems have a sense of self, which gives them consciousness. Machines with self-awareness understand their own current state. This type of AI does not yet exist.
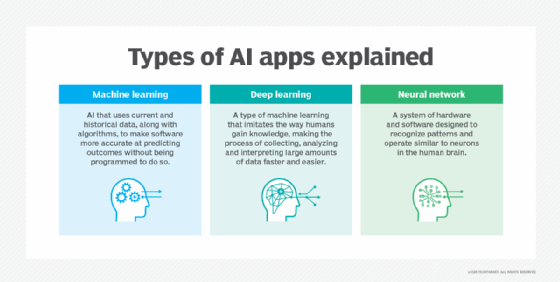
- Machine Learning:
- Developed to mimic human intelligence. It lets the machines learn independently by ingesting vast amounts of data and detecting patterns. Many ML algorithms use statistics formulas and big data to function.
- Type of artificial intelligence (AI) that allows software applications to become more accurate at predicting outcomes without being explicitly programmed to do so. Machine learning algorithms use historical data as input to predict new output values.
- Recommendation engines are a common use case for machine learning. Other popular uses include fraud detection, spam filtering, malware threat detection, business process automation (BPA) and Predictive maintenance.
- Classical machine learning is often categorized by how an algorithm learns to become more accurate in its predictions. There are four basic approaches: supervised learning, unsupervised learning, semi-supervised learning and reinforcement learning. The type of algorithm data scientists choose to use depends on what type of data they want to predict.
- Deep Learning:
- Subset of machine learning. Deep learning enabled much smarter results than were originally possible with machine learning. Consider the face recognition example.
- Deep learning makes use of layers of information processing, each gradually learning more and more complex representations of data. The early layers may learn about colors, the next ones learn about shapes, the following about combinations of those shapes, and finally actual objects. Deep learning demonstrated a breakthrough in object recognition.
- Deep learning is currently the most sophisticated AI architecture we have developed.
- Computer Vision:
- Computer vision is a field of artificial intelligence (AI) that enables computers and systems to derive meaningful information from digital images, videos and other visual inputs — and take actions or make recommendations based on that information.
- The most well-known case of this today is Google’s Translate, which can take an image of anything — from menus to signboards — and convert it into text that the program then translates into the user’s native language.
- Machine Vision:
- Machine vision is the ability of a computer to see; it employs one or more video cameras, analog-to-digital conversion and digital signal processing. The resulting data goes to a computer or robot controller. Machine vision is similar in complexity to voice recognition.
- Machine vision uses the latest AI technologies to give industrial equipment the ability to see and analyze tasks in smart manufacturing, quality control, and worker safety.
- Computer vision systems can gain valuable information from images, videos, and other visuals, whereas machine vision systems rely on the image captured by the system’s camera. Another difference is that computer vision systems are commonly used to extract and use as much data as possible about an object.
- https://searchenterpriseai.techtarget.com/definition/AI-Artificial-Intelligence +
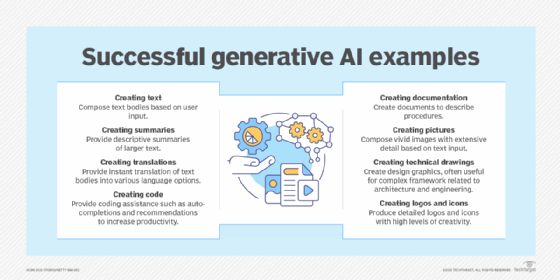
- Generative AI:
- Generative AI technology generates outputs based on some kind of input – often a prompt supplied by a person. Some GenAI tools work in one medium, such as turning text inputs into text outputs, for example. With the public release of ChatGPT in late November 2022, the world at large was introduced to an AI app capable of creating text that sounded more authentic and less artificial than any previous generation of computer-crafted text.
- Edge AI Technology:
- Edge artificial intelligence refers to the deployment of AI algorithms and AI models directly on local edge devices such as sensors or Internet of Things (IoT) devices, which enables real-time data processing and analysis without constant reliance on cloud infrastructure.
- Simply stated, edge AI, or “AI on the edge“, refers to the combination of edge computing and artificial intelligence to execute machine learning tasks directly on interconnected edge devices. Edge computing allows for data to be stored close to the device location, and AI algorithms enable the data to be processed right on the network edge, with or without an internet connection. This facilitates the processing of data within milliseconds, providing real-time feedback.
- Self-driving cars, wearable devices, security cameras, and smart home appliances are among the technologies that leverage edge AI capabilities to promptly deliver users with real-time information when it is most essential.
- EtherCAT:
- The Ethernet Fieldbus: https://www.ethercat.org/default.htm + EtherCAT is the open real-time Ethernet network originally developed by Beckhoff. EtherCAT sets new standards for real-time performance and topology flexibility.
- EtherCAT Technology Group:
- The worlds largest Industrial Ethernet organization with 6900 member companies: https://www.ethercat.org/en/tech_group.html + The ETG is a global organization in which OEM, End Users and Technology Providers join forces to support and promote the further technology development. The EtherCAT Technology Group keeps EtherCAT technology open for all potential users.
- Ethernet:
- Ethernet is a family of wired computer networking technologies commonly used in local area networks, metropolitan area networks and wide area networks. It was commercially introduced in 1980 and first standardized in 1983 as IEEE 802.3.
- Single Pair Ethernet (SPE):
- Single Pair Ethernet cables are copper cables that only contain one twisted pair (single pair) that they use for data transmission, for example in industrial applications.
- Describes the transmission of Ethernet over only one pair of twisted copper wires. In addition to data transmission via Ethernet, SPE also enables a simultaneous power supply of terminal devices via PoDL – Power over Data Line.
- As its name suggests, Single Pair Ethernet (SPE) cabling uses only one pair of wires to transmit data, as opposed to the two pair that have long been standard in the majority of Ethernet cabling in use worldwide.
- Single Pair Ethernet System Alliance:
- https://singlepairethernet.com/en/
- The Single Pair Ethernet System Alliance is a worldwide association of leading technology companies. We want to implement and further develop the pioneering Single Pair Ethernet technology. Together and holistically.
- The Single Pair Ethernet System Alliance is an ever-growing, collaborative community. Technology companies from all over the world jointly drive the further development of SPE technology and its implementation in various applications.
- Founding Members are: Weidmüller, Phoenix contact, Rosenberger, Datwyler, Draka and R&M
- Single Pair Ethernet:
- Single-Pair Ethernet, or SPE, is a new Ethernet communication standard for factory, process, and building automation that will enable a more rapid deployment of integrated strategies, such as the Industrial Internet of Things.
- Conventional Ethernet which is based on industrial applications requires two or four pairs of wires. In comparison Single Pair Ethernet only has one pair. Compared to the four and eight wires in conventional Ethernet cable categories this two-wire design cuts cabling weight nearly in half.
- PoE (Power over Ethernet):
- Power over Ethernet (PoE) is the process of sending electrical power and data over copper wire. The combination of data transmission along with power supplying hardware onto the same RJ45 Ethernet connector allows for the transmission of power over the network cabling.
- As PoE technology has developed, the amount of power that can be sent over Ethernet cable has increased. IEEE-compliant PoE switches and injectors can output anywhere from 12 watts to over 70 watts of power per port.
- Carbon Dioxide (CO2):
- Primary greenhouse gas emitted through human activities. Carbon dioxide enters the atmosphere through burning fossil fuels (coal, natural gas, and oil), solid waste, trees and other biological materials, and also as a result of certain chemical reactions (e.g., manufacture of cement). Carbon dioxide is removed from the atmosphere (or “sequestered”) when it is absorbed by plants as part of the biological carbon cycle.
- Biogenic Carbon Dioxide (CO2):
- Carbon Dioxide released as a result of the combustion or decomposition of organic material, that is biomass and its derivatives. Examples include carbon dioxide released during the combustion of wood and biogas generated by decomposition.
- Biogenic Carbon Dioxide (CO2) and Carbon Dioxide (CO2) are the same. Scientists differentiate between biogenic carbon (that which is absorbed, stored and emitted by organic matter like soil, trees, plants and grasses) and non-biogenic carbon (that found in all other sources, most notably in fossil fuels like oil, coal and gas).
- Carbon Capture and Storage (CCS):
- CCS involves the capture of carbon dioxide (CO2) emissions from industrial processes, such as steel and cement production, or from the burning of fossil fuels in power generation. This carbon is then transported from where it was produced, via ship or in a pipeline, and stored deep underground in geological formations.
- CCS projects typically target 90 percent efficiency, meaning that 90 percent of the carbon dioxide from the power plant will be captured and stored.
- Decarbonization:
- Reduction of carbon dioxide emissions through the use of low carbon power sources, achieving a lower output of greenhouse gasses into the atmosphere.
- Carbon Footprint:
- There is no universally agreed definition of what a carbon footprint is. A carbon footprint is generally understood to be the total amount of greenhouse gas (GHG) emissions that are directly or indirectly caused by an individual, organization, product, or service. These emissions are typically measured in tonnes of carbon dioxide equivalent (CO2e).
- In 2009, the Greenhouse Gas Protocol (GHG Protocol) published a standard for calculating and reporting corporate carbon footprints. This standard is widely accepted by businesses and other organizations around the world. The GHG Protocol defines a carbon footprint as “the total set of greenhouse gas emissions caused by an organization, directly and indirectly, through its own operations and the value chain.”

